Code42 Incydr Detects Corporate Data Exfiltration Movement to Personal Google Drive, Box, Other Cloud Applications
Today, 91% of security leaders believe that users are exfiltrating data through personal cloud accounts, yet nearly half (49%) don’t have a tool to differentiate personal and corporate cloud application uploads. As cloud-based collaboration tools have risen in popularity within the enterprise, personal use of the same tools has become a breeding ground for insider data leaks and theft, contributing to losses up to 20% of revenue annually.
This type of insider risk is growing increasingly common and is a challenging data security blind spot.
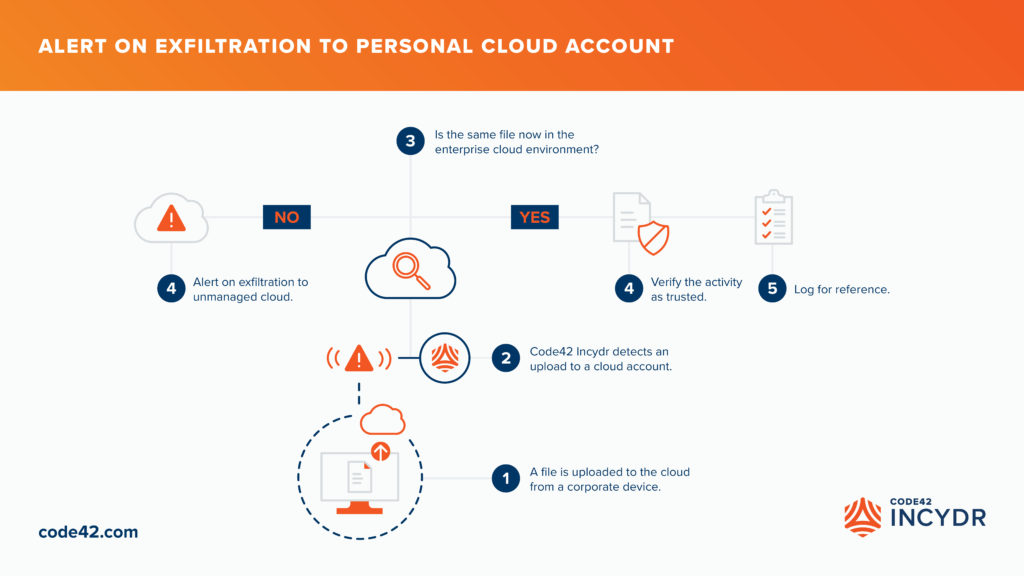
Code42 Incydr’s new functionality reduces alert noise of data movement to authorized sanctioned applications while alerting on data exfiltration to unsanctioned destinations, such as personal cloud apps.
The product enhancement does not require configuration by administrators, changes to network infrastructure or policy implementation.
 “The innovative way that Incydr pinpoints file exfiltration to personal cloud accounts is a game changer. Businesses today are facing an unprecedented confluence of risk to their organizations. We’re seeing the biggest workforce shifts in history, a growing sense of personal ownership over work produced, and the portability of data has only increased – especially with the adoption of cloud-based consumer and enterprise tools,” said Joe Payne, Code42 president and CEO. “Incydr quickly identifies which users are moving data to personal Google Drive and Box accounts, ensuring that organizations are protected from insider data exfiltration.”
“The innovative way that Incydr pinpoints file exfiltration to personal cloud accounts is a game changer. Businesses today are facing an unprecedented confluence of risk to their organizations. We’re seeing the biggest workforce shifts in history, a growing sense of personal ownership over work produced, and the portability of data has only increased – especially with the adoption of cloud-based consumer and enterprise tools,” said Joe Payne, Code42 president and CEO. “Incydr quickly identifies which users are moving data to personal Google Drive and Box accounts, ensuring that organizations are protected from insider data exfiltration.”
The Code42 Incydr data risk detection and response product provides a prioritized view of the highest-risk data exposure and exfiltration events happening across organizations. By monitoring all file computer, cloud and email activity through an endpoint agent and API-to-API integrations with corporate data systems, the Code42 Incydr product is able to determine whether or not a file in motion is put in a trusted or untrusted cloud destination.
This feature builds upon Code42’s innovative Browser Upload capability, which detects and alerts security teams to unauthorized browser upload activity.
“When it comes to clearly identifying if source code or trade secrets are being uploaded to an unsanctioned place, like a personal cloud account, many times organizations rely on domain-based methods as an approach. The challenge with apps like Google Drive is that there aren’t unique sub-domains for enterprise and personal environments, so security cannot clearly and swifty distinguish if data is at risk or not,” added Rob Juncker, Code42 CTO. “We’re validating when files reach their expected enterprise destination within the corporate environment and, more importantly, when they do not.”
