
ME-ISAC: How to Protect Yourself and Your Organization From Phishing
Based on the huge number of phishing attacks seen over the past year, it is more important than ever to detect, educate and defeat these attacks on an organization’s employees and infrastructure, according to Chris Taylor, director of the Media & Entertainment Information Sharing & Analysis Center (ME-ISAC).
Speaking during the Security & WFH breakout presentation “Ahab and the Great Whale Phish” May 12 at the annual Hollywood Innovation and Transformation Summit (HITS) Spring event, he noted that ME-ISAC provides threat intelligence sharing and information security analysis, and serves as the “fusion point that ties all of the different media and entertainment companies together.”
 ME-ISAC operates as an initiative within the Content Delivery & Security Association (CDSA) for the benefit of the Trusted Partner Network (TPN).
ME-ISAC operates as an initiative within the Content Delivery & Security Association (CDSA) for the benefit of the Trusted Partner Network (TPN).
“We watch all the evil on the Internet and then report it out to all of our membership,” according to Taylor. “Part of that involves us bringing in data from a lot of public sources [and] bringing in data from the federal government” – the U.S., as well as Canada and the U.K., he said.
“We try to take in all of these streams of data from all over the place, bring it in to one place [and] curate that stream so that we remove the duplicates,” he explained. ME-ISAC focuses on those things that are “pertinent to the media and entertainment industry and then provide that stream back out to you,” he noted, adding: “One of our data sources is all of you” and that data can benefit all members.
When there is an attack that ME-ISAC reports information on, it keeps the identity of the victim anonymous, he pointed out. If the victim shares information about the bad actor responsible for the attack, ME-ISAC will share the information with other members “so that everybody can raise their shields and try to inoculate themselves,” he said.
The Phishing Threat
Among the “evil that we’re tracking… phishing is one of the largest threats facing all of us on the Internet right now,” Taylor said, adding: “We look at a lot of different phishing attacks and then add those indicators into our stream.”
In phishing attacks, the bad actors are typically trying to steal user names and passwords or deliver malware, he noted. If the phishing attack is “very targeted,” that is called “spear phishing,” he said. In a spear phishing attempt, the email may mention your company’s name, he noted.
A “typical” non-targeted phishing email, on the other hand, will go out to many people claiming to be, for example, a DHL shipping notice, he said.
 Then there are whale phishing attempts that are even more targeted than spear phishing attacks and may include a signature block that is copied from a company’s executive and sent to employees at that firm, he added.
Then there are whale phishing attempts that are even more targeted than spear phishing attacks and may include a signature block that is copied from a company’s executive and sent to employees at that firm, he added.
There are also many phishing attacks that are sent via text messages on smartphones, as well as on social media sites, he said, adding: “If there’s a way to communicate with you, there are people trying to use that as a vehicle to do something evil.”
Business Email Compromise (BEC), meanwhile, is a “broader category that includes phishing and other cons [and] fraud that occurs in email-related attacks,” he noted.
“The vast majority of the malware that we find when we go in and do some type of incident response… comes in through email,” he explained, adding: “Most of the cybercrime groups that are trying to steal credentials or steal credit card and financial information or conduct other types of fraud [are] use phishing emails as the primary way that they attack people and a lot of times they’re going to put a link” in their emails in the hope that the recipient will click on that link and go to a website operated by that bad actor.
“The vast majority of the new websites that are registered every single day are being used maliciously [and are] either hosting one of these fake websites to harvest credentials or they’re delivering malware to somebody,” he warned.
The Numbers
A whopping 94% of malware is delivered by email, according to ME-ISAC, citing a Verizon 2019 Data Breach Investigations Report.
 Meanwhile, 65% of cybercrime gangs use phishing as their primary method, according to Symantec 2019 Internet Security Threat Report.
Meanwhile, 65% of cybercrime gangs use phishing as their primary method, according to Symantec 2019 Internet Security Threat Report.
And 70% of newly-registered domains are malicious, according to Palo Alto Unit 42 research.
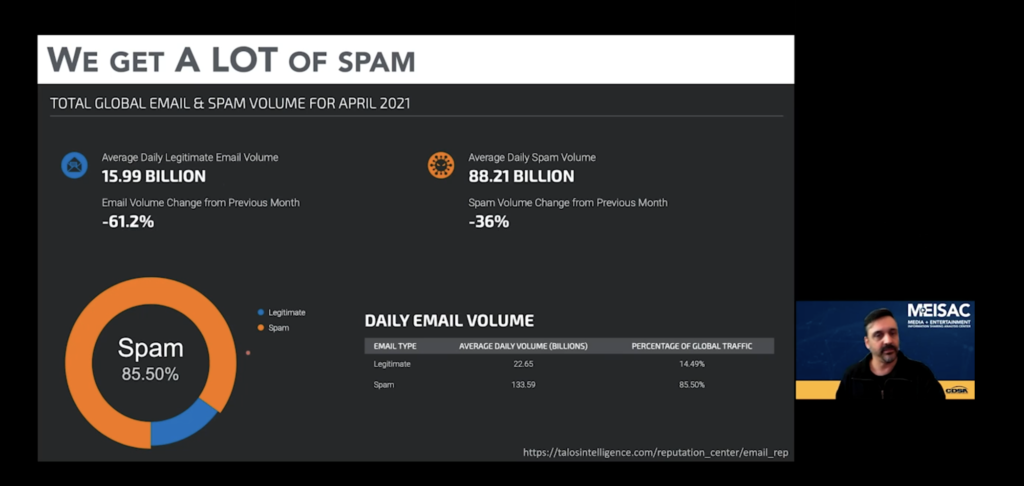
According to April 2021 data from Cisco Talos Intelligence, the average daily legitimate email volume was 15.99 billion and was easily outpaced by the average daily spam volume of 88.21 billion.
What You Can and Should Do
Reporting “evil” email is important because it helps determine what email is legitimate and what isn’t so that it can then be blocked, Taylor explained.
He suggested that everybody run short tests when they receive emails that include:
- Look at the from address. Often times, a phishing email is pretending to be from DHL or, to a lesser degree, Federal Express, Amazon and other companies that ship products. A “red flag” for you is when it is not the legitimate company’s actual domain that is used.
- Look at the to address. Is it the one you use for shipping notifications? Taylor noted that he uses one email address specifically when he ships products.
- What is the context of the email?
- What is the format of the message? Is it what a real email from that company normally looks like? Is the company’s logo missing? Is the spelling off?
- Do you trust the attachment? Most legitimate companies do not email you executable files to run on your desktop.
“The ones that really scare me” have no attachment or link and will often pretend to be your company’s CEO but it’s coming from an email that is not the CEO’s email, Taylor said, noting that many people are scammed into thinking their boss needs certain information that is requested.
Concluding, he summed up what you can and should do when you receive emails:
- Slow down.
- Always consider the context of emails.
- Don’t click links or open attachments if there is any doubt about who sent it to you.
- Report phishing emails by using your email client’s “Report Message” button because that report will help your organization’s or email service provider’s security team tune their filters.
- Use a good spam filter/Secure Email Gateway that filters out the “evil.”
To download the presentation slides, click here.
To view the entire presentation, click here.
HITS Spring was presented by IBM Security with sponsorship by Genpact, Irdeto, Tata Consultancy Services, Convergent Risks, Equinix, MicroStrategy, Microsoft Azure, Richey May Technology Solutions, Tamr, Whip Media, Eluvio, 5th Kind, LucidLink, Salesforce, Signiant, Zendesk, EIDR, PacketFabric and the Trusted Partner Network.
