
HITS Spring: IBM Security CTO Details When to Consider ‘Zero Trust’
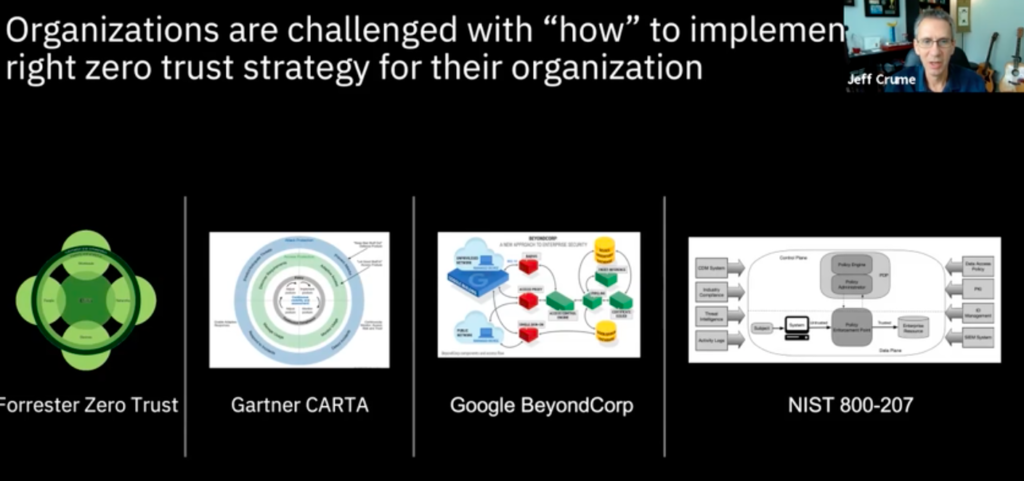
On May 12 at the annual Hollywood Innovation and Transformation Summit (HITS) Spring event, Jeff Crume, distinguished engineer, CTO of the Americas for IBM Security, and an IBM master inventor, shared a slide showing just how complicated the concept of “zero trust” has become.
Four different groups — from Google to Gartner — are implementing their zero trust strategies in four completely different ways. And not a single one of them is going about it in the wrong way, Crume said.
“It depends on risk analysis,” he said during the opening presentation “Securing Everything: An Introduction to Zero Trust.” “It’s your understanding of what’s at stake, what would be the consequences of loss or compromise, what are the costs to secure [it].”
 The roots of the “zero trust” concept go back nearly two decades, born out of the Jericho Forum an international group established in 2004 that promoted de-perimeterisation, and the idea that you must assume the network is hostile.
The roots of the “zero trust” concept go back nearly two decades, born out of the Jericho Forum an international group established in 2004 that promoted de-perimeterisation, and the idea that you must assume the network is hostile.
Today, the term zero trust covers an evolving set of network security paradigms, ones that move network defences from broad network perimeters to focusing narrowly on individual and groups of resources. No implicit trust is granted to systems based on their physical or network locations, access to data resources is only granted when that resource is absolutely required, and authentication — for both users and devices — only happens before a connection is established.
But just like you wouldn’t just leave everything open, you don’t necessarily need to triple-lock and chain up everything either, Crume said. One side is “ not even ‘we don’t lock the front door,’ it’s ‘ we don’t have a front door,’” he added. “Zero trust in the extreme would be ‘we have everything locked down with multiple locks.’” Zero trust carries certain inherent costs and limitations, and striking the right balance between high-minded principles and real-world pragmatism is the challenge, he said
“In reality, not everything calls for that extreme,” Crume said said. “That’s why I talk about this in terms of a measure of graded trust. We want to have the right level of security based on the sensitivity of the information and resources that are there. Not everything needs the full gamut of security capabilities, and very few things need to be put out there for free for everyone to have.”
IBM is now helping its customers adopt the right zero approach to their security, introducing a new Software-as-a-Service (SaaS) version of its IBM Cloud Pak for Security, one designed to simplify how companies deploy a zero trust architecture across the enterprise. To learn more, click here.
HITS Spring was presented by IBM Security with sponsorship by Genpact, Irdeto, Tata Consultancy Services, Convergent Risks, Equinix, MicroStrategy, Microsoft Azure, Richey May Technology Solutions, Tamr, Whip Media, Eluvio, 5th Kind, LucidLink, Salesforce, Signiant, Zendesk, EIDR, PacketFabric and the Trusted Partner Network.
