
A new report on malicious advertising underscores the importance of using modern web browsers and making sure your operating system is up to date with the latest security updates to prevent being infected.
When threat actors perform malicious advertising, or malvertising, they target their ads at specific web browsers and operating systems.
For example, malvertisers pushing exploit kits will show ads to Internet Explorer users as they target the browser's vulnerabilities and ads pushing the Mac Shlayer Trojan will only show the ads to macOS users.
Based on the analysis of 378 million blocked malicious ads over three months between Oct. 15, 2019 - Jan. 15, 2020, Confiant illustrates how companies and government agencies are targeted based on the browsers or operating systems that they use.
Some govt agencies continue to use Internet Explorer
Every month on Patch Tuesday, Microsoft releases new security updates and there are invariably new vulnerabilities fixed in Microsoft's outdated Internet Explorer browser.
These vulnerabilities are commonly targeted by exploit kits to install ransomware, password-stealing Trojans, remote access Trojans (RATs). or other malware, yet we continue to see organizations use this browser and potentially have their networks compromised.
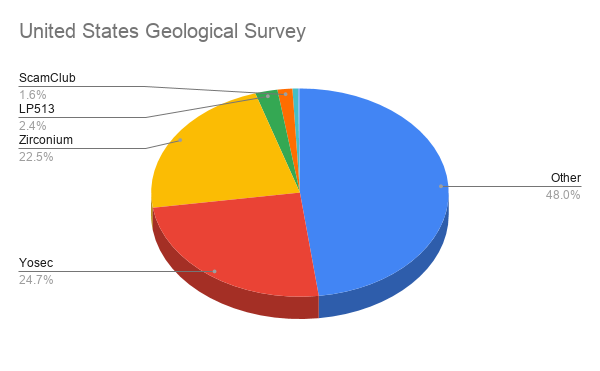
In Confiant's report, they illustrate how both the United States Geological Survey and the United States Postal service are both heavily targeted by malvertising campaigns by Zirconium and Yosec.
 |
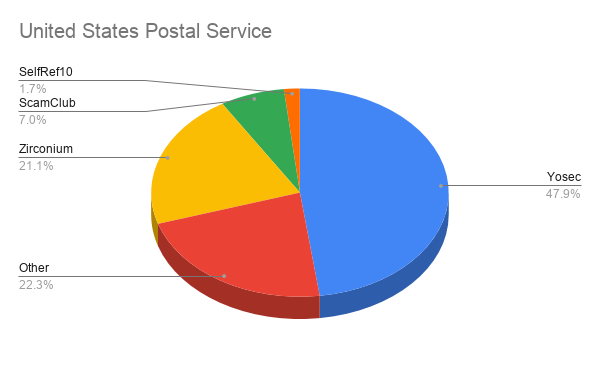 |
Confiant Security researcher Eliya Stein explains that the malvertisers are not specifically targeting these two government agencies, but rather the technology that they using.
For example, Zirconium is known to be heavily targeted at outdated browsers to show tech support scam pages, so it is likely both the USGS and USPS are using outdated browsers.
"Our hypothesis is easily confirmed when we pull reporting by browser — 23% of traffic recorded from the Geological Survey is Internet Explorer, but only 1.6% for the Senate," Confiant states in their report.
Both organizations also have a high percentage of malvertising attacks by the Yosec malvertising group. As this group targets Macs with scams and fake updates pushing the Shlayer Trojan, it shows that both organizations utilize a larger amount of macOS devices compared to other U.S. government agencies.
Macs targeted more in Fortune 100 companies
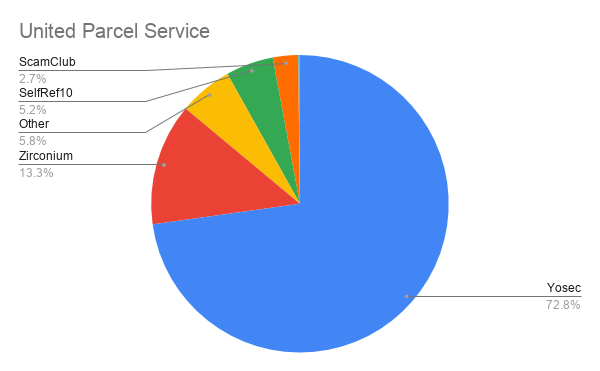
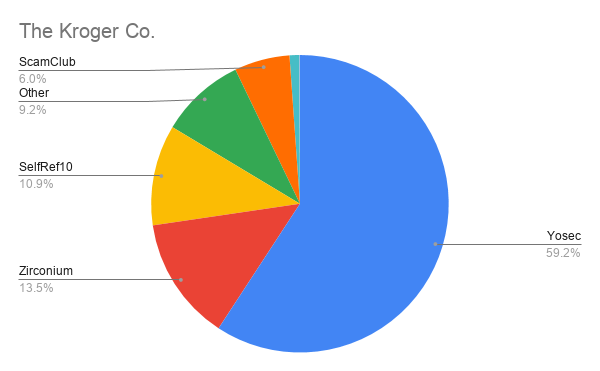
The monitored malvertising campaigns also offer us insight into the types of computers and browsers Fortune 100 companies are using.
In a corporate setting, it is not surprising that we begin to see a much larger percentage of malvertising from the Yosec group who target Mac computers.
For example, Apple, The Kroger Co., UPS, Boeing, and MetLife have over 50% of their malvertising attacks targeting Mac computers indicating that these companies utilize a large amount of Mac computers compared to other companies.
 |
 |
Numerous other companies such as Anthem Blue Cross Blue Shield, PepsiCo, and State Farm also are heavily targeted by Yosec with over 40% of their malvertising attacks directed at Mac computers.
Outdated browsers also remain a huge problem for the Fortune 100 companies where we see Zirconium continue to take a huge market share of the malvertising attacks.
For example, Home Depot, Chevron, and FedEx have over 40% of their malvertising attacks being directed towards outdated browsers.
This continues to illustrate how the enterprise needs to move their employees and applications from outdated web browsers such as Internet Explorer towards modern browsers that provide a more secure auto-updating mechanism.
Malvertising can lead to a compromised network
Most malvertising tends to involve nuisance redirects to fake giveaways, tech support scams, and adult sites, but it could also have more dire consequences.
With the continued usage of outdated browsers, exploit kits could use vulnerabilities to install malware that allows attackers to gain access to the network.
From there, they can exfiltrate files, steal corporate secrets, compromise more devices, and eventually deploy ransomware throughout the network.
Unfortunately, while updating your browser to a modern version will increase security and block some of the attacks, Stein told BleepingComputer that malvertisers will just switch to a different targeting method.
"Updating browsers is important, but at the same time I think that the attackers will just use something else for targeting purposes," Stein told BleepingComputer.
Government agencies and the enterprise should instead increase their overall security posture through the use of security software (even on Macs), web filtering services, ad blockers, and threat intelligence services.


Comments
NoneRain - 4 years ago
MS should announce the removal of IE from Win10 in a future build. They should start digging the pit right after the new Edge is deployed.
Some-Other-Guy - 4 years ago
"Some govt agencies continue to use Internet Explorer"
----------------------------------------------------------------
Then they deserve ransomware, password-stealing Trojans, remote access Trojans (RATs). and other malware
Perpetual updates are not needed
Just ban the use of software from Microsoft and other Companies that perpetually cause these problems
If you can ban the use of Huawei due to National Security Threats, then we can certainly do it to Microsoft for the same reason