
Rooster Teeth Productions have suffered a data breach that allowed attackers to steal credit card and other payment information from shoppers on the company's online store.
The production company, known for its popular shows and documentaries such as RTDocs, Crunch Time, Red vs. Blue, gen:LOCK, and Day 5, suffered an attack that redirected shoppers to a fake payment form on checkout.
According to a data breach notification, Rooster Teeth discovered on December 2nd that their online store was hacked earlier that day. As part of this hack, a malicious script was injected into the store that would cause the shopper to be redirected to a fake payment page under the control of the attackers.
"On December 2, 2019, Rooster Teeth discovered that malicious code had been added to the Site earlier the same day. The malicious code directed users entering a checkout on the Site to a spoofed webpage where they were asked to enter payment card details in order to complete their purchases. This was inserted after the stage at which users entered their shipping data. Users who completed the payment card details page were then directed to the real webpage, where they were asked to complete the forms again."
This allowed the attackers to steal a customer's name, email address, telephone number, physical address, and/or payment card information that was submitted.
This malicious code was removed from their store on the same day.
Rooster Teeth has sent data breach notifications to customers who were affected by this breach and are offering a free 1-year Experian IdentityWorks subscription.
For those who were affected, BleepingComputer strongly suggests that you contact your credit card merchant and explain the situation. You should also monitor your statements for any fraudulent or suspicious charges and dispute them immediately if detected.
Not a common Magecart attack
Most online store credit card stealing attacks that we have seen recently are called Magecart attacks and involve compromising an online store to inject malicious scripts. These scripts will then quietly monitor for submitted credit card information and then send it a remote 'drop' site under the attacker's control so that it can be collected.
Yonathan Klijnsma of RiskIQ told BleepingComputer that Rooster Teeth was affected by an attack similar to ones that were recently disclosed in the researcher's Full(z) House: a digital crime group report.
In the attack described in Full(z) House and Rooster Teeth's data breach notification a malicious script was combined with a phishing page under the attacker's control to steal the payment information.
For example, below is a fake Commonwealth Bank phishing page that is used to steal payment information from Australian customers in attacks like this.
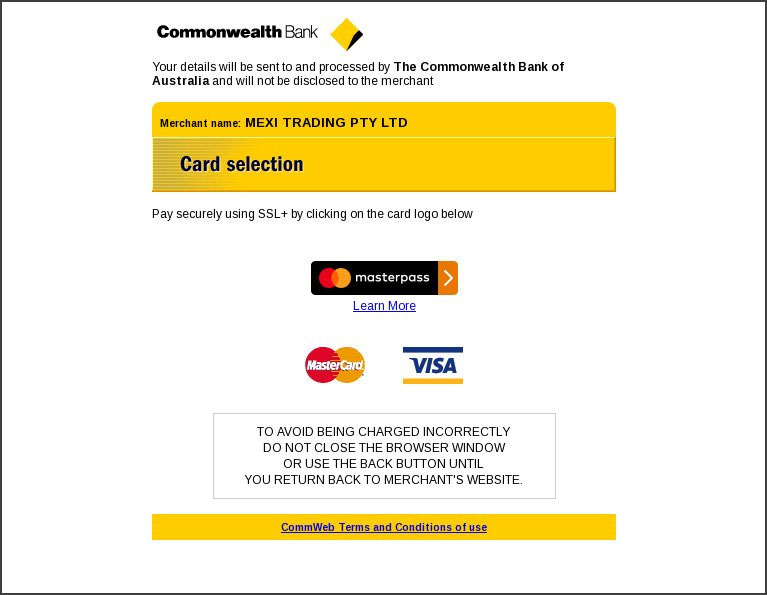
Malwarebytes' Jérôme Segura, who first spotted the phishing trick used in these attacks, told BleepingComputer that this attack utilizes a variety of different phishing pages depending on the geographic region of the shopper.
Below are a list of domains Segura stated are used in these attacks:
payment-mastercard[.]com
google-query[.]com
google-analytics[.]top
google-smart[.]com
google-payment[.]com
jquery-assets[.]com
sagepay-live[.]com
google-query[.]com
payment-sagepay[.]com
payment-worldpay[.]com
When a user clicked on the button to make a payment, instead of being shown the store's normal payment page, they would be redirected to a fake payment page pretending to be for a credit card merchant but is under the attacker's control.
This is similar to a legitimate redirect a user may encounter when purchasing items on stores that process payments through Google Pay or PayPal.
When the shopper submits the payment information, it is transmitted to the attacker's server where it can be collected later. The phishing page then redirects the user back to the store's legitimate payment checkout page where the customer will be prompted to submit the information again.
While not a traditional Magecart attack, it does achieve the same result. It also shows us that the attackers are constantly evolving their operations to use new attack scenarios and methods that we must be aware of.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now