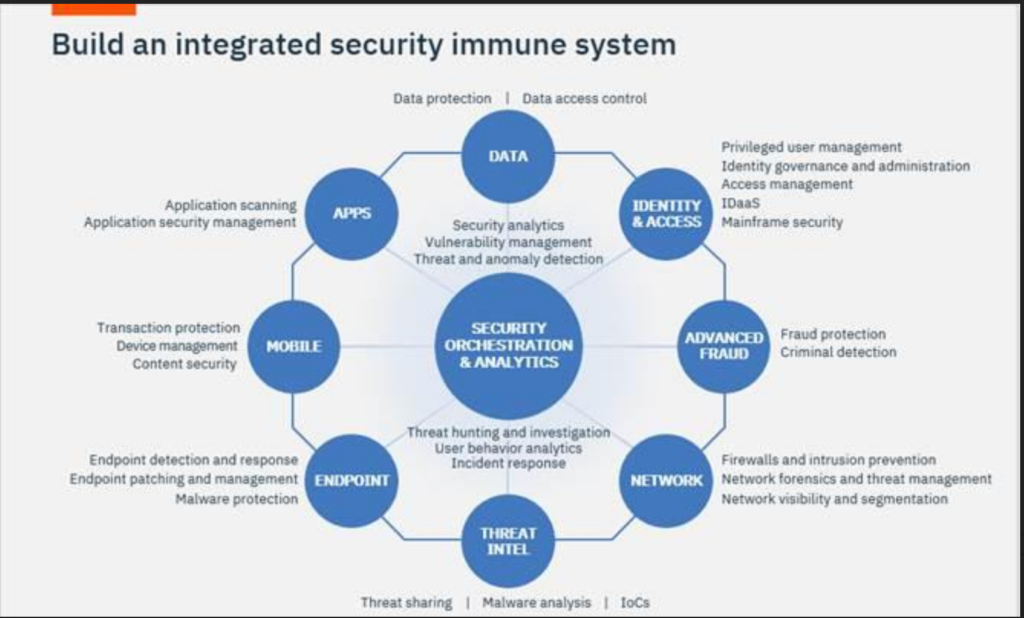
IBM Security’s portfolio of enterprise security products and services runs the gamut, covering applications, mobile, networks, data, the cloud, you name it, all centered around enabling organizations to better manage risk and defend against emerging threats.
IBM Security monitors approximately 60 billion security events per day in more than 130 countries, and for the media and entertainment side, helps industry organizations with both general IT and distribution solutions, and helps them create robust security programs.
Patrick Vowles, team lead of North America marketing for IBM Security, spoke with the Media & Entertainment Services Alliance (MESA) about the origins of IBM’s security division, how artificial intelligence comes into play with security, and the cybersecurity challenges confronting media and entertainment companies the most today.
MESA: How did the IBM Security division come about, and what gaps in the security market has the company sought to fill?
 Vowles: IBM Security was created to concentrate and integrate IBM’s security capabilities and products into one cohesive unit. Cybersecurity is one of IBM’s “Strategic Imperatives” (of focus/importance to the company as a whole) and IBM Security itself is now an over $2 billion division of IBM, making it a highly significant player in this space.
Vowles: IBM Security was created to concentrate and integrate IBM’s security capabilities and products into one cohesive unit. Cybersecurity is one of IBM’s “Strategic Imperatives” (of focus/importance to the company as a whole) and IBM Security itself is now an over $2 billion division of IBM, making it a highly significant player in this space.
Due to the breadth of security products and services, IBM Security is able to help establish a complete security program for our clients, with or without utilizing our own products. This is a clear differentiator from most other vendors in the security space that can often only address one specific area or challenge with one point product.
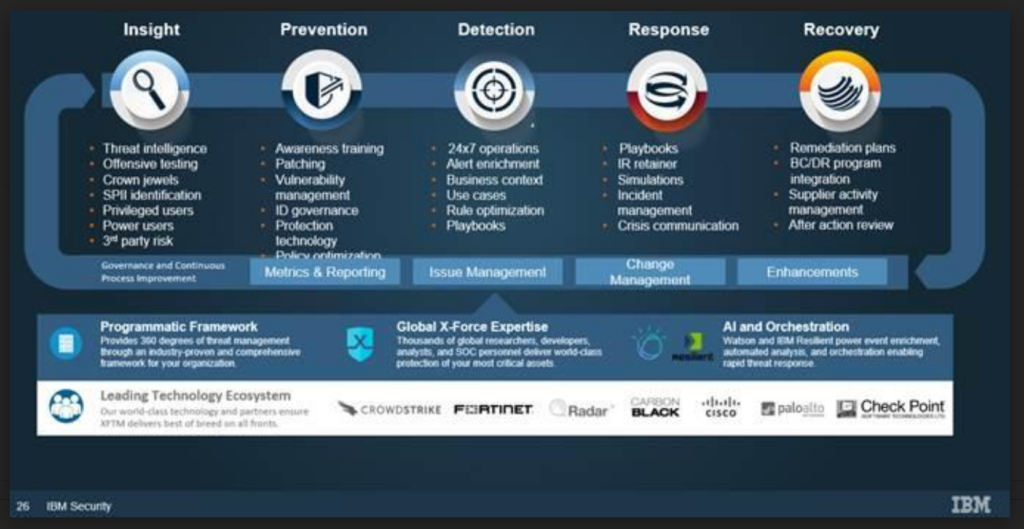
The IBM Security “Immune System” offers our clients the option of allowing us to help them build, update or simply augment their existing security program.
The attackers execute a highly sophisticated and well-structured attack, from reconnaissance all the way through to compromise and exfiltration/destruction of data. No single security solution can protect against that, so it is imperative that a highly structured, layered defense, must be built and tested in response.
MESA: What does IBM Security offer that’s unique in terms of monitoring threats and insider attacks, and how can media and entertainment companies make use of these services?
Vowles: The “detect” portion of security programs is mostly centered around a Security Information and Event Management (SIEM) solution such as our QRadar platform. This central platform correlates potentially billions of individual events per day down to a small number of suspicious “incidents” (a group of associated events), that a security analyst needs to investigate. These analysts are often overwhelmed with information and struggle to research and identify actual, active attacks in their environment and often waste a great deal of time on investigating false positives. IBM Security can dramatically improve the efficiency and precision of security incident investigation by layering on advanced analytics such as user behavior and network flow analysis, even Watson based AI. Watson for Cybersecurity is constantly updating its understanding of the threat landscape and can apply that knowledge to an incident to help analysts identify real attacks far more quickly.
No other vendor can offer this breadth and depth of analysis, whether an organization wishes to leverage an on-prem or cloud-based solution. These analytics capabilities also integrate with our Guardium suite, which discovers databases (a primary depository of proprietary information and therefore often a target for attack), helps harden, encrypt and manage access to them.
 MESA: How does IBM marry Watson to its security services, to help identify and prevent attacks?
MESA: How does IBM marry Watson to its security services, to help identify and prevent attacks?
Vowles: QRadar Advisor with Watson is continuously updating its understanding of the threat landscape by consuming terabytes of structured and unstructured threat intelligence such as articles, blogs, whitepapers, dark web chat rooms and security alerts that no human could possibly keep up with. The AI function also develops an understanding of the behavior of malicious actors and can rapidly compare all this information with activity our SIEM platform is observing in the network.
The insights provided can cut investigation and analysis time from days or weeks to minutes or hours. In effect it is a security analyst that knows almost as much as there is to know, with instant and total recall. This quickly helps eliminate false positives and drastically improves the efficiency and precision of security teams.
MESA: Securing portable electronic devices and IoT are huge topics in the M&E industry today. What does IBM Security offer to help clients confront these potential threats?
Vowles: For mobile devices we have a number of applicable offerings, from complete Mobile Device Management (MDM) from our MaaS360 solution, a variety of Identity and Access Management (IAM) options through to data security solutions. This allows us to fully secure mobile endpoints, strictly control authentication to sensitive data, as well as layer on other data security functions such as encryption, database hardening and access control and auditing. Due to the variety of IoT operating systems and often very poor “built in” security, it is difficult to secure those devices themselves, but we can control to a very granular level, what data they have access to and how they use it and limit the impact of those IoT devices being compromised.
 MESA: What are some of IBM Security’s favorite media and entertainment use case examples, where M&E firms made especially good use of the company’s services?
MESA: What are some of IBM Security’s favorite media and entertainment use case examples, where M&E firms made especially good use of the company’s services?
Vowles: We are lucky to have many telecommunication, media and entertainment organizations as our clients where IBM helps them with general IT and distribution solutions and IBM Security helps them create far more robust security programs. As M&E organizations move to open, IP-based technologies for collaboration, creation and distribution, they are entering a domain where even the most sophisticated of the world’s security practitioners continue to struggle to defend their assets against a highly capable range of adversaries.
IBM Security is working with some of the largest organization on the planet to help secure their infrastructure and is able to apply those capabilities directly to M&E businesses.
MESA: What’s next for IBM Security, what advances and innovations is the company looking forward to?
Vowles: There are many, often AI-based advancements in the pipeline, but the vast majority of breaches are successful because organizations are not effectively implementing many of the fundamentals of information security to help ensure the Confidentiality, Integrity and Availability of their data. Many organizations need a great deal of help in building a complete foundational security program, then we can talk about AI.
Vowles has more than 25 years of hands-on IT and security product management and marketing experience. He has created many innovative connectivity, security and compliance solutions for major vendors including an entire set of managed security and remote access services for a global ISP. He has also managed virtualization and cloud security product offerings while contributing to such projects as those run by the Cloud Security Alliance. He now leads a team of portfolio marketers at IBM Security. [email protected]
