Widespread news reports about recently-discovered security vulnerabilities known as Meltdown and Spectre have many M&E security executives looking for answers about how severe a problem this actually is and what their recommended remediation actions should be.
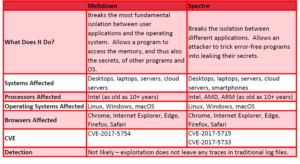
Last year, Google in cooperation with university researchers identified a large security vulnerability with designs commonly employed to improve microprocessor performance. By using a technique known as “speculative execution,” these CPUs avoid running unnecessary calculations and, thus, perform chains of commands much faster.
However, modern processors from AMD, Intel, ARM that are hardcoded to use speculative execution can leak information about commands that do not end up being run, allowing programs (using Linux, Windows, MacOS operating systems) to glimpse the protected parts of the operating system’s memory and making it possible for hackers to exploit security bugs or expose secure information such as passwords or stored files.
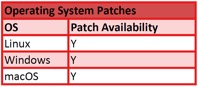
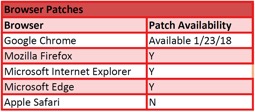
Meltdown and Spectre patches for the Linux and Microsoft platforms are already available. For MacOS, Apple has stated that 10.13.2 patches this vulnerability. However, some experts advise that software updates alone will not completely resolve problem; thus, it is important to make sure that the latest computer bios/firmware updates are installed as well. It also has been reported that some of the recently developed patches can downgrade processor performance anywhere from five-to-35%.
While several M&E companies have categorized the risk associated with these vulnerabilities as “High,” as of this week, there have been no news reports of the vulnerability being exploited
The following charts often a comparative breakdown of the vulnerabilities and remediation options for Meltdown and Spectre that are being discussed online and in the literature:
Meltdown and Spectre At-a-Glance:
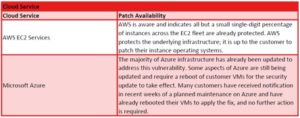
Patch Availability (please note that vendors are actively addressing these vulnerabilities and information may quickly become dated):
Sources/Additional Information:
- Google Project Zero vulnerability advisory: https://googleprojectzero.blogspot.com/2018/01/reading-privileged-memory-with-side.html
- The Hacker News: “Meltdown and Spectre CPU Flaws Affect Intel, ARM, AMD Processors”:https://thehackernews.com/2018/01/meltdown-spectre-vulnerability.html
- InfoSec Handlers Diary Blog: “Spectre and Meltdown: What You Need to Know Right Now”:https://isc.sans.edu/diary/rss/23193
- Meltdown and Spectre: Bugs in modern computers leak passwords and sensitive data”: https://meltdownattack.com/
- Microsoft Support: “Windows Server Guidance to protect against the speculative execution side-channel vulnerabilities”:https://support.microsoft.com/en-gb/help/4072698/windows-server-guidance-to-protect-against-the-speculative-execution
- Bleeping Computer: “List of Meltdown and Spectre Vulnerability Advisories, Patches, & Updates”:https://www.bleepingcomputer.com/news/security/list-of-meltdown-and-spectre-vulnerability-advisories-patches-and-updates/
- redhat: “Speculative Execution Exploit Performance Impacts – Describing the performance impacts to security patches for CVE-2017-5754 CVE-2017-5753 and CVE-2017-5715”: https://access.redhat.com/articles/3307751
- Cyberscoop: “Industry Braces for critical Intel security flaw impacting a decade’s worth of chips”:https://www.cyberscoop.com/intel-chip-flaw-virtual-memory-microsoft-windows-linux/
- Gizmodo: “Report: All Intel Processors Made in the Last Decade Might Have a Massive Security Flaw”: https://gizmodo.com/report-all-intel-processors-made-in-the-last-decade-mi-1821728240
- The Register: “Kernel-memory-leaking Intel Processor design flaw forces Linux, Windows redesign”:https://www.theregister.co.uk/2018/01/02/intel_cpu_design_flaw/