The cybersecurity skills gap, defined as a shortage of qualified people needed to fill open positions in IT security, is a phenomenon that I have researched quite extensively this year, and with good reason. You may have seen this recent headline:
"Donald Trump Advised to Train 100,000 Hackers to Protect the US"
I don't like the way that headline was worded, but I'm in agreement with the underlying point: the US President's Commission on Enhancing National Cybersecurity has strongly recommended that the country "should increase ... efforts on training security experts that would work for the country and not leave for the private sector, which has become a dramatic problem in the last few years" (Softpedia). And you may have seen other headlines, like this one from Forbes at the start of this year: "One Million Cybersecurity Job Openings In 2016". This is a problem that is negatively impacting governments, companies, non-profits, and even consumers (inadequate IT security staffing can lead to data breaches that expose your information).
Yes, the cybersecurity skills gap is that big
Having studied the numbers from multiple perspectives, I agree that the world is probably in need of one million more people with cybersecurity skills than are currently available to hire. The US alone needs something like 200,000 more people skilled in cybersecurity, and I'm not talking about the people that IT security managers want to hire but can't get budget for. The skills gap is a shortfall in qualified applicants for funded positions.
I discussed the numbers and definitions in a paper that I presented in October to one of the longest running annual computer security conferences, Virus Bulletin. Yesterday VB published the paper online. I also included the skills gap in my 2017 Trends webinar earlier this week (registration required). So why this concern for the skills gap? It is clear to me that it is undermining the security of many organizations. How many? At least two thirds is my assessment, maybe more.
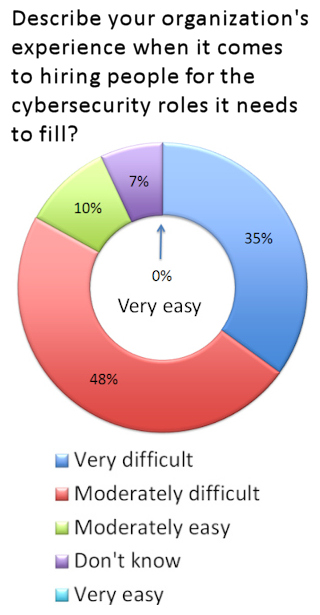 Let's consider some data points. Four different surveys by four different entities found a remarkably consistent threshold number when they asked IT executive and managers at a wide range of organizations if they thought there was a shortage of cybersecurity professionals: 80%.
Let's consider some data points. Four different surveys by four different entities found a remarkably consistent threshold number when they asked IT executive and managers at a wide range of organizations if they thought there was a shortage of cybersecurity professionals: 80%.
There are ISACA and (ISC2)2 numbers from 2015 and 2016 in the low- to mid-80s. An Intel-McAfee sponsored study published in July by CSIS - the Center for Strategic and International Studies - had 82%. The results of my own survey, fielded in July, can be seen on the right. Add up those who said moderately difficult or very difficult and you get? Tada! 83%. You will also note that nobody said that their cybersecurity hiring very easy.
I was particularly pleased to see the CSIS study, and not just because CSIS was one of the first organizations to raise the alarm about the skills gap (A Human Capital Crisis in Cybersecurity - PDF). In addition to assessing the perceived size of the problem, CSIS looked at how many organizations considered the skills shortage to be responsible for "direct and measurable damage". The answer was a fairly shocking 71%! This led to CSIS Fellow James A. Lewis to a conclusion with which I strongly concur: “A shortage of people with cybersecurity skills results in direct damage to companies, including the loss of proprietary data and IP” (Hacking the Skills Shortage).
Closing the skills gap
A critical analysis of efforts to close the cybersecurity skills gap was the subject of my master's degree dissertation that will be published next year, but there is definitely some good news on this front. Much of this good news is thanks to a series of presidential initiatives on cybersecurity during the Obama administration, starting in 2009 with the launch of NICE, the National Initiative on Cybersecurity Education. This organization's mission, which is coordinated by the National Institute of Standards and Technology (NIST), is: "to improve the nation's cybersecurity education, including [but by no means limited to] efforts directed at the federal workforce". NICE has since worked with public and private experts and organizations, federal agencies, and industry partners to develop the National Cybersecurity Workforce Framework as a necessary first step. (Disclaimer: I serve on the NICE Industry Advisory Board.)
The goal of the Workforce Framework is to establish a standard taxonomy that can be used "to describe all cybersecurity work and workers irrespective of where or for whom the work is performed". By 2014, NICE had resolved cybersecurity work into 31 specialist areas organized into seven categories: securely provision; operate and maintain; protect and defend; investigate; collect and operate; analyse; and oversight and development. The next phase was to identify the knowledge, skills and abilities, the KSAs, required for each role. The combined results are available in various formats, including an impressive 127-page hyperlinked PDF that enables employers and job seekers to drill down to the competencies required for different roles. The Workforce Framework has also been published as a NIST 800 series document (800-181).
Last month I attended the 7th annual NICE conference and learned about a whole slew of new cybersecurity degrees, apprenticeships, and competitions. All of these are feeding efforts to close the skills gap and you can read about many of them by downloading the conference papers. A major announcement was the launch of the CyberSeek.org website which ties together a lot of these efforts and is well worth a look, whether you're a manager seeking to hire or someone thinking of cybersecurity as a career.
What can you do?
If you're a cybersecurity professional who enjoys this field of endeavor, please encourage others to join our ranks! If you're an organization struggling to hire cybersecurity talent, I can offer some quick tips (on which I promise to expand in a follow-up article next year). Over the past 12 months I have spoken to numerous organizations facing this problem. Sometimes it's because of budget constraints - in a market-based economy, scarcity leads to higher prices. Location can also be a factor - not everyone with the skills you need to hire will necessarily want to move to where you need them to be.
My advice is to play to your strengths as an employer when hiring, while also cultivating internal talent. What makes working at your organization attractive? Maybe you're more rural than hi-tech hot spot, but not all cybersecurity professionals are looking for a big city job. My gut tells me that some of the more dedicated security folks, those for whom the work is as much a calling as a career, could be tempted to more low-key locations, particularly if there are good connectivity options. You might also want to consider remote hires, which can work for a wide range of cybersecurity roles.
The biggest single attraction for current and aspiring cybersecurity professionals is probably a high level of commitment to security, which is also something that brings many other benefits to your organization. Make this clear in your hiring efforts, let folks know that security efforts at your firm have the backing of the board and the management, and that security talent is valued and nurtured.
Because current efforts to close the skills gap will take time to bear fruit, organizations should seriously consider fostering internal talent, growing your own cybersecurity professionals. There is no shortage of training courses and conferences from which current employees can benefit, whether your goal is to turn a network admin into a security person, or you're looking to retain existing cybersecurity talent (in my experience, the benefits of sending the right employees to the right events far exceed the costs).
Another tip is for IT security managers to work closely with Human Resources when hiring for “the cyber”. Do not assume that the folks in HR know how to advertise or screen for this type of job. I've heard from a lot of security folks that the "laundry list" style of job posting is a total turn off. And please pay attention to the requirements. Do you really need a CISSP? (I have written about the CISSP question here.) Your focus should be on the work that job applicants have demonstrated they can perform, not pieces of paper. Some of the best long-term hires may be folks who come to you without degrees or certs but get them while working for you.




